If you are trial counsel presenting, for example, DNA or scientific accident reconstruction evidence, you would be sure to have a good command of such evidence. Not that a PhD in such subjects is required, but a competent understanding from at least a layman’s perspective would enable an effective direct or cross-examination. Nothing more than basic trial preparation.
Unfortunately, the prosecution in the Zimmerman trial did not meet this standard. Yesterday, while questioning key witness Jenna Lauer, prosecutor Bernie de la Rionda lugged his laptop up to the witness stand and clumsily poked around Lauer‘s Twitter account. He sought to paint Lauer as a Twitter follower of Robert Zimmerman, the defendant‘s brother, thus suggesting bias. Unfortunately, de la Rionda lacked a general command of how Twitter worked, including a basic understanding of a follower versus a followee on Twitter, and Lauer was able to get away with denying she was following Robert Zimmerman. (Video of this trial exchange here – at the 8:20 mark).
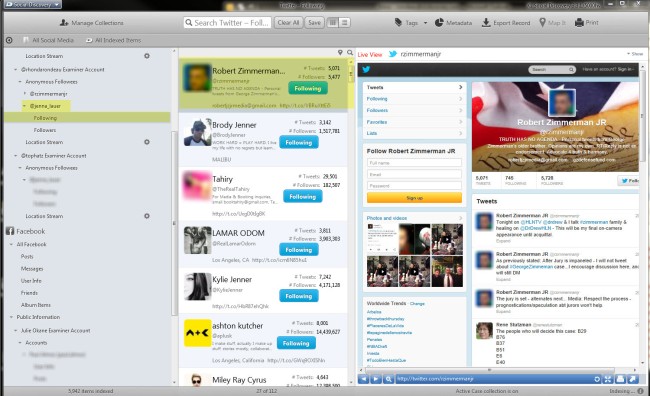
In truth, Lauer was in fact following Robert Zimmerman and, in an apparent recognition that she may have committed perjury, deleted her Twitter account shortly after her testimony. Below is a screenshot establishing who Lauer was following, obtained from the silent follow feature of X1 Social Discovery, which collected and preserved all tweets and other publically available account information only hours before Lauer deleted the account from Twitter. This evidence clearly reflects that George Zimmerman’s brother was in fact followed by the witness.
By now it should be obvious to every trial lawyer that utilizing best practice tools that not only collect and preserve this key social media evidence in a silent and defensible manner but also enable the presentation of such key social media evidence at trial — without having to share your laptop with the witness out of the view of the jury — is required. As attorney John Browning, a partner at Lewis Brisbois, pointed out earlier on this blog, any attorney who does not leverage the mountains of social media evidence available in nearly all cases may be violating their ethical duty of competence.
I don’t know what the local rules are for the Zimmerman courtroom, but the above screenshot from X1 Social Discovery would have made an effective visual. Evidence on social media accounts establishing that a party or witness has friended or is following a particular party is routinely used to establish bias establish connections to our knowledge of that person or subject matter. There are mountains of clues and subtle inferences that can be derived from such information with the right tools and requisite degree of understanding of social media, and the attorneys and investigators who have the competency to leverage this information gain the upper hand.
And as it turns out, social media evidence is relevant to the testimony of the two most important witnesses in the Zimmerman case thus far. Travon Martin’s friend and “star” prosecution witness Rachel Jeantel apparently deleted portions of her twitter account in the past few days to allegedly cover-up incriminating and off color tweets. The lesson here is that social media evidence is not only relevant to the direct parties to a litigation but also key witnesses as well as jurors.